)
Using QR codes in phishing, or “quishing,” is an increasingly popular phishing technique in a post-pandemic world. We tested out a free quishing tool to see how easy it is for attackers.
Driven by the pandemic, QR codes, shorthand for "quick reference” codes, have increasingly been adopted as a simple, contactless method of sharing and accessing digital content. While sharing URLs is the most common use for QR codes, the codes can also store other information. Other common uses for QR codes are to store authentication links, contact information, calendar data, geolocation data, and plain-text information.
The rise in QR code usage has led to their use in phishing attempts by threat actors. Also known as “quishing,” threat actors take advantage of our trust in QR codes and use them to mislead, steal information and credentials, and bypass security measures. Across the underground, we can see a growing number of threat actors requesting and advertising quishing services (Figure 1).
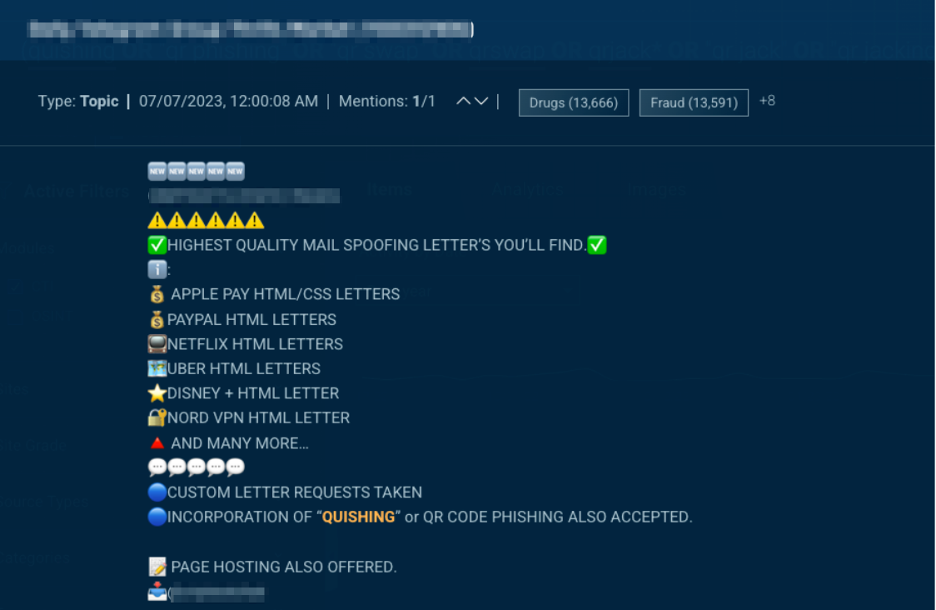 Figure 1. QR phishing or “quishing” is advertised as part of a phishing service in the underground.
Figure 1. QR phishing or “quishing” is advertised as part of a phishing service in the underground.
Security teams are still seeking a consistent methodology to defend against these attacks (Figure 2). As QR codes are images, QR-related attacks are much more likely to bypass many phishing prevention tools that check for text patterns and links standard in traditional phishing attempts. Users scan QR codes with their smartphones, which adds to the complexity. With increased chances of success, it’s clear why threat actors are leaning into using QR codes.
 Figure 2. A user expresses their struggles to defend their organization against QR phishing attacks.
Figure 2. A user expresses their struggles to defend their organization against QR phishing attacks.
Tools of the Trade
While many quishing attacks include QR codes in existing phishing templates, more advanced quishing tools are shared underground. These tools allow threat actors to share dynamic QR codes to steal multifactor authentication tokens or trick less cautious users into approving remote authentication attempts, sometimes called QR Jacking (Figure 3.)
 Figure 3. A tool shared on the underground using QR codes to attack Discord users.
Figure 3. A tool shared on the underground using QR codes to attack Discord users.
EvilQR
To demonstrate the capabilities of these tools, we downloaded an open-source tool called EvilQR. EvilQR uses a browser extension and a server script to dynamically serve QR codes as quishing pages that trick a victim into allowing a threat actor to log in to the victim’s account.
After downloading the tool from Github, we ensured our environment had the latest versions of the Google Chrome browser and Go programming language. In Chrome’s extension settings, we enabled developer mode, clicked “Load Unpacked,” and selected the extension folder from the EvilQR files to add the EvilQR extension to the browser (Figure 4).
 Figure 4. The EvilQR extension loaded into the Chrome browser.
Figure 4. The EvilQR extension loaded into the Chrome browser.
Next, we built and ran the server that hosts the quishing pages using the provided scripts. To build the server, we navigated in a terminal to the “server” folder in the EvilQR files and ran chmod 700 build.sh && ./build.sh. To run the server, we ran the following in a terminal from the main directory of the EvilQR files: ./server/build/evilqr-server -d /server/templates (Figure 5).
 Figure 5. Running the EvilQR server.
Figure 5. Running the EvilQR server.
EvilQR has a few prebuilt quishing page templates for specific sites that use QR codes to authenticate, such as Discord. We went to Discord’s login page and activated the EvilQR extension, which copies the Discord authentication QR code tied to the browser session. In a separate browser, we visited the site hosted on our local machine by the EvilQR server at 127.0.0.1:35000 to find a quishing page with a copy of our QR code (Figure 6).
 Figure 6. (Left) Discord login page, with optional QR code authentication. (Right) A quishing page dynamically pulls the QR code from the Discord login page.
Figure 6. (Left) Discord login page, with optional QR code authentication. (Right) A quishing page dynamically pulls the QR code from the Discord login page.
The quishing page, when shared, attempts to trick victims by disguising the Discord authentication QR code as an invitation to join a Discord channel. However, if scanned and accepted, the code will log the threat actor’s original browser session into the victim’s account instead.
To show what the victim would see, we used our phone to scan the QR code on the quishing page, which takes us to a screen asking if we want to log in on another device (Figure 7).
 Figure 7. Scanning the QR code on the quishing site sends a login request to the victim.
Figure 7. Scanning the QR code on the quishing site sends a login request to the victim.
Pressing ‘Log in’ will log the threat actor into the victim’s account. Discord helpfully provides a warning here, but not every site will. Careless users can quickly become victims by accepting without reading what’s happening.
Conclusion
The cyber underground continues to provide a variety of avenues and opportunities for threat actors to engage in malicious activities. Free, easy-to-use tools are widely available, and actors can deploy them in successful attacks. A curious threat actor with an appetite for cybercrime can inflict a lot of damage.
Fortunately, organizations can take measures to defend themselves. Here are a few tips to proactively defend against quishing attacks.
Add content about QR code risks to security training and awareness programs
Verify senders of emails and don’t scan QR codes from unknown senders, or avoid scanning QR codes entirely if possible
Encourage users to check the URL shown by the camera or scanning application before opening the linked site
If using a phishing prevention tool, check to see what protections are available for QR-based attacks
Monitor underground channels to detect phishing and quishing templates, tools, and services targeting your organization with real-time, comprehensive threat intelligence
And finally, if targeted phishing is called spear phishing, is targeted quishing called spear quishing or squishing?
Do you want to learn about the proactive measures you can take to protect your organization from phishing and quishing schemes? Request a demo.
)
)
)
)